Week 1 - Pump Up Your Password
Week 1 - Pump Up Your Password
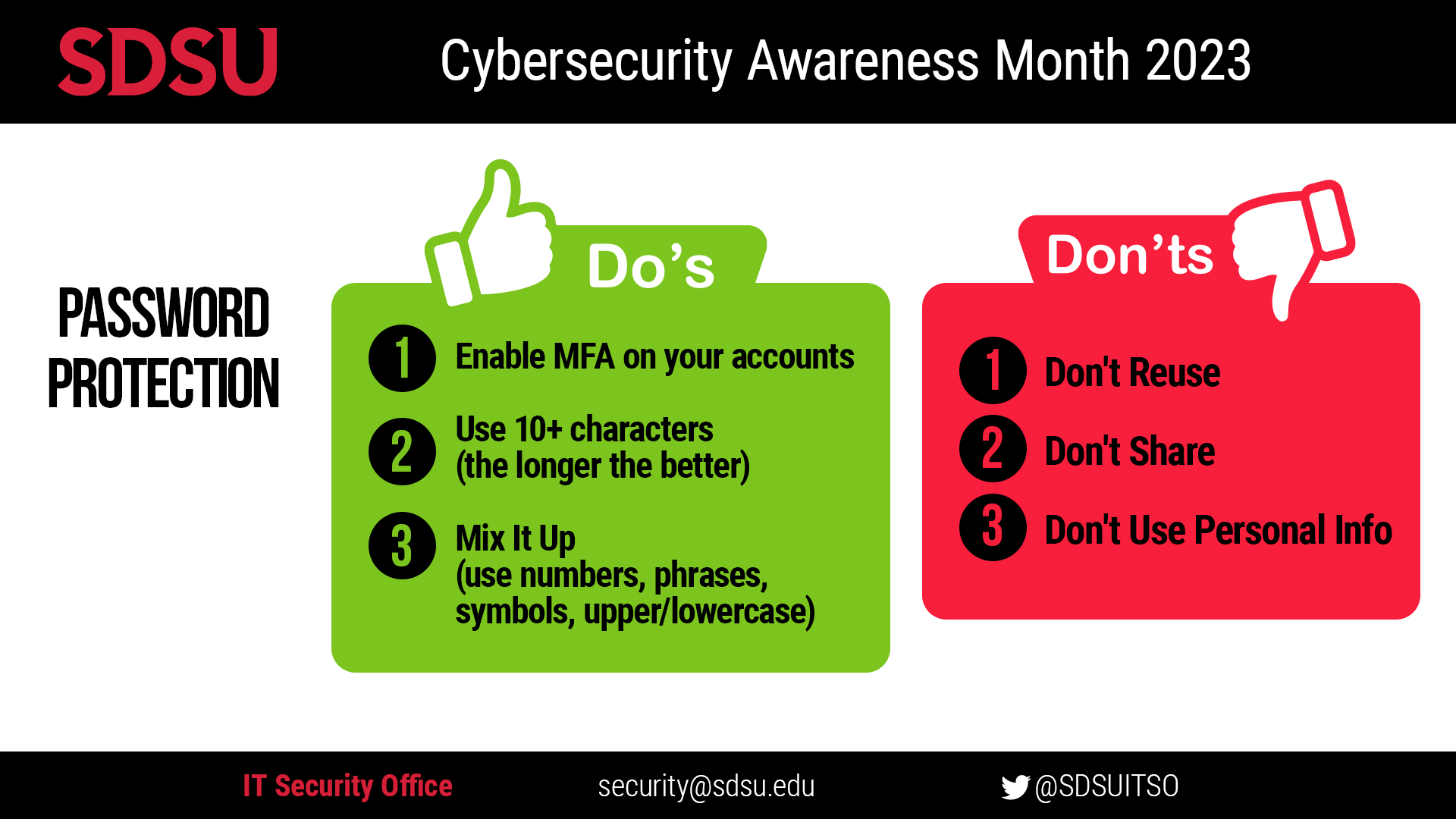
Strong passwords are the key to protecting your online, digital life. A 2022 report by NordPass of the most common passwords used around the world revealed that “123456,” “qwerty,” and “password” were still the most common passwords used by individual users. All of these types of passwords can be cracked in under one second. Follow these security tips and more below to ensure you are protecting your password.
Security Tips on password protection
-
Create a complex password: Passwords should contain uppercase and lowercase letters, numbers 0 through 9, and non-alphanumeric characters, and be at least 10 characters. Do not allow repetitive or sequential characters (e.g. ‘aaaaaa’, ‘abc123’).
-
Use a long passphrase: According to the National Institute of Standards and Technology (NIST) guidance, you should consider using the longest password or passphrase permissible. For example, you can use a passphrase, such as a news headline or even the title of the last book you read. Add some punctuation and capitalization for extra complexity.
-
Don’t make passwords easy to guess: Do not include personal information in your passwords, such as names of relatives or pets. This information is often found on social media sites, making it easier for cybercriminals to hack your accounts.
-
Avoid using common words: Substitute letters with numbers and punctuation marks or symbols. For example, @ can replace the letter “A” and an exclamation point (!) can replace the letters “I” or “L.”
-
Keep your passwords on the down-low: Don’t tell anyone your passwords and watch for attackers trying to trick you into revealing your passwords through email or calls (social engineering).
-
Unique account, unique password: Having different passwords for various accounts helps prevent cybercriminals from gaining access to these accounts and protects you in the event of a breach.
Remembering My Password is so Hard!
The most secure way to store all your unique passwords is by using a password manager. A password manager generates and remembers different, complex passwords for each of your accounts and encrypts them for additional security.
You have choices. Remember to compare your options and look for a quality password management system:
-
Encryption: Quality password managers encrypt all of the passwords stored on them. This means that your passwords would be basically impossible to decode if a hacker tried to breach your password manager. The only access to your passwords on a password manager is with a password only you know.
-
Multi-Factor Authentication: Because your password vault on a password manager is so valuable, the best password managers require multi-factor authentication for you to log in. This means that anyone trying to view your passwords from unfamiliar device will need to log in multiple ways, such as facial ID, fingerprint scan, inputting a code you get in an SMS text message or approving the log-in attempt on a separate app.
-
Zero Knowledge: As the name suggests, zero knowledge means a password manager does not know what your password is – the company does not store the keys needed to decrypt the main password that unlocks your vault. This means that your main password is never kept on the system’s servers. You are the only one who knows it, so you should make it strong and protect it with MFA.
Source: https://staysafeonline.org/online-safety-privacy-basics/password-managers/
Have I Been Pwned?
In Hacker speak, the word "pwned" is typically used to imply that someone has been controlled or compromised, for example "I was pwned in the Adobe data breach".
Ever wonder if your email account or phone number has been involved in a data breach? Check out Have I Been Pwned to see whether your personal data has been compromised by data breaches. This site collects and analyzes hundreds of database dumps and pastes containing information about billions of leaked accounts, and allows users to search for their own information by entering their username or email address. Users can also sign up to be notified if their email address appears in future data dumps in the dark web.